The cybersecurity environment has grown intricate due to the widespread adoption of multi-cloud infrastructures and the expansion of remote work environments.
Today, most enterprises leverage multiple cloud service providers spanning Infrastructure as a Service (IaaS), Software as a Service (SaaS), and Platform as a Service (PaaS) models. Moreover, individual applications often operate across various cloud service models offered by diverse providers. For instance, envision a service-based application that encompasses functionalities such as data storage, processing, and user authentication, each potentially sourced from distinct cloud providers. This scenario exemplifies the intricate interplay of diverse service providers and models within modern applications.

What is Cybersecurity Mesh?
The proliferation of cloud technologies and the decentralization of workforces triggered by events like the COVID-19 pandemic have further exacerbated this fragmentation. As a result, there has been a surge in demand for distributed technologies and the widespread adoption of geography-agnostic services like SaaS.
Traditional security architectures struggle to cope with the threats imposed by these evolving conditions. This calls for a paradigm shift in cybersecurity measures. In this scenario, cybersecurity mesh has emerged as a promising solution, alleviating the reliance on a singular computing environment.
Cybersecurity Mesh Architecture (CSMA) is not a specific technology. It is an architectural strategy, similar to the concept of zero trust. While zero trust assumes that every device within an ecosystem is potentially compromised and hostile, CSMA views environments as disparate, logically separated, and heterogeneous. This distinction, while oversimplified, is fundamental to CSMA.
In Gartner’s `Top Strategic Technology Trends for 2022: Cybersecurity Mesh,’ CSMA is outlined as a composable and scalable method for extending security controls, even to widely distributed assets. According to the report, companies implementing a cybersecurity mesh architecture can expect to diminish the financial ramifications of security incidents by approximately 90% by 2024.
It enables security tools to integrate through a set of enabling services, including distributed identity fabric, security analytics, intelligence, automation and triggers, centralized policy management, and orchestration.
As per insights shared by Adam Hils, an analyst at Gartner, the cybersecurity mesh architecture integrates various cybersecurity solutions from a single vendor. This integration extends beyond firewalls, encompassing a broader spectrum of security tools. In alignment with the increasing adoption of zero trust architectures, organizations can synchronize their firewall systems and implement a least-trust approach for enhanced security measures.
Gemini Consulting & Services specializes in assisting enterprises in harnessing cutting-edge technologies, prioritizing people, processes, and culture to establish a resilient and continually evolving security framework tailored to your business needs. Our primary objective is to mitigate risks and revamp your enterprise security to suit the demands of a dynamic business landscape.
Through a proactive approach, we offer a comprehensive multi-layered cybersecurity solution encompassing strategic planning, risk management, thorough risk assessments, threat intelligence analysis, incident response protocols, advanced malware and ransomware defence mechanisms, as well as continuous security monitoring services. Leveraging our extensive global experience, we excel in implementing cybersecurity solutions from renowned industry leaders such as McAfee, Cisco, IBM, Microsoft, and Fortinet.
Gemini Consulting & Services can help your enterprise from cyber threats triggered due to multi-cloud adoption. Contact us to know how your organization can leverage cybersecurity mesh.
Short-Term Effects of Cybersecurity Mesh
CSMA consists of four distinct layers:
- Security analytics and intelligence
- Distributed identity fabric
- Consolidated policy and posture management
- Consolidated dashboards
When considering these layers in the context of multi-cloud and remote work scenarios, the implementation of security policies across various cloud service providers can significantly differ. For instance, managing a secret in Microsoft Azure Key Vault differs from AWS Cloud HSM or Google Cloud Key Management due to variations in API, administration, and security models. Despite these technical disparities, the overarching policy objectives, such as secrets management, remain consistent across providers.
Hence, consolidated policy and posture management tools are invaluable in translating abstract policy objectives into specific configurations across different providers. These tools ensure that policies regarding cryptographic key access, for instance, are consistently enforced across diverse environments.
Also, effective security monitoring requires the aggregation and analysis of telemetry data across environments, alongside insights into assets and threats. This necessitates the integration of analytics and intelligence to provide holistic security insights.
Lastly, in a distributed environment, identity management becomes crucial. Users or customers should not have to repeatedly authenticate when accessing applications spread across different Platform as a Service (PaaS) or Infrastructure as a Service (IaaS) environments. Thus, the identity fabric must span across various environments to ensure seamless access.
The short-term impacts of cybersecurity mesh may not immediately alter the day-to-day routines of practical-minded practitioners. Currently, they have access to various products facilitating the foundational aspects of CSMA (Cybersecurity Mesh Architecture), as outlined by Gartner. Additionally, organizations are aligning their strategies with multi-cloud and remote work scenarios to separate policy enforcement, break down security silos, and adjust to a more permeable and fragmented security perimeter. Some even adopt architectures that discard the traditional perimeter concept entirely.
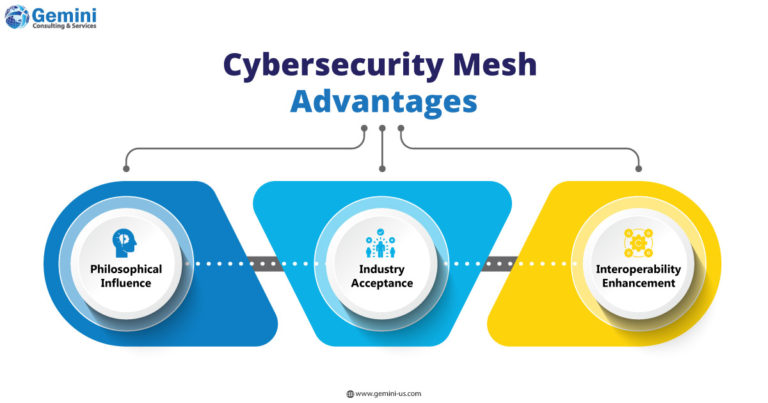
Philosophical Influence: Market dynamics, influenced by philosophical shifts, often shape real-world architectures. For instance, the adoption of zero trust, originating in the mid-1990s but gaining traction since Google and Forrester Research endorsed it, has spurred innovation among tech companies and driven initiatives in end-user organizations.
Industry Acceptance: Wide acceptance within the industry streamlines the incorporation of concepts into architectural approaches. Just as zero trust gained credibility over time, the recognition of CSMA as a viable architectural strategy can simplify discussions around multi-cloud, hybrid cloud, orchestration, and containerization security. This acceptance prompts organizations to acknowledge the complexity of modern cloud interrelationships, leading to budget allocations for enhanced monitoring and intelligence gathering across overlooked environments like private and hybrid clouds.
Interoperability Enhancement: Acknowledging the role of environmental differences in cloud security promotes interoperability. Abstract policies tied to specific configurations, along with synchronized, normalized monitoring information from various providers, mitigate issues such as vendor lock-in. These outcomes collectively contribute positively to cybersecurity.
In summary, while the short-term impact of cybersecurity mesh may seem limited, its long-term implications promise significant benefits for practitioners, shaping both philosophical approaches and industry practices while enhancing interoperability in cybersecurity ecosystems.