Enterprises are increasingly using the metaverse to enhance engagement and user experience. Although the metaverse hasn’t fully materialized yet, it’s crucial for companies to devise strategies as it can lead to new challenge, especially in terms of cybersecurity.
While the core ideas and benefits of the metaverse are known to most people, there has been relatively little focus on the potential cybersecurity risks and privacy concerns associated with this emerging virtual segment.
In this blog, we explore some of the privacy and security challenges that companies may encounter when embracing the metaverse, and we look at strategies on how to prepare for them proactively.
What is the metaverse?
The metaverse can be described as a virtual space where individuals connect, interact, and engage in commerce. This fusion of the physical and digital spheres is captured by the term “meta,” meaning beyond or transcending, combined with “verse,” derived from universe.

The metaverse primarily manifests in two forms:
Virtual Reality (VR): VR technology offers users an artificial reality experience through specialized headsets that immerse them in a virtual environment. This immersion can extend to audio and body tracking, allowing users to interact with the virtual world using their hands or other body movements.
Augmented Reality (AR): AR is less immersive compared to VR and involves overlaying virtual elements onto the real-world using devices like lenses or screens. Users retain a view of their physical surroundings while interacting with virtual elements. Examples of AR include smartphone apps like Waze or wearable devices such as Microsoft’s HoloLens, which provide location-based information and contextual overlays.
It’s important to note that, in VR environments, privacy expectations are currently limited, whereas in AR settings, where interactions are intertwined with the physical world, privacy considerations are more pronounced.
Implementing cybersecurity measures in the metaverse involves addressing three key components: the security of the hosting platform, the security of property owners (renters), and the security of users within the virtual environment. Let’s look at the main risks associated with each component and propose ways to mitigate them.
Platform Owners: One significant risk is the lack of consistent regulations governing cybersecurity practices across different metaverse platforms. This issue can lead to fragmented user experiences and uncertain security standards. To address this, platform owners should collaborate to formulate unified set of regulations and commit to stringent security protocols. This can drive platform adoption and trust. Additionally, implementing a proactive and reactive security strategy supported by artificial intelligence can help identify and address potential threats. Establishing channels for users and property owners to report security issues is also important for ensuring a secure environment.
Property Owners/Renters: A key challenge for property owners and renters in the metaverse is the lack of awareness regarding cybersecurity best practices. Many users may be unfamiliar with the security features of the platform they’re using, leading to potential vulnerabilities. To address this risk, property owners should educate themselves about platform security features and ensure they implement appropriate security measures for their virtual properties. It is essential for companies to use user-friendly language to communicate with users on security policies. If not, user might not understand their rights and responsibilities regarding data privacy. Property owners must also be transparent about the types of user data collected and provide clear information about data usage and rights.
Consumers/Users: Consumers face risks related to personal data privacy and credential verification in the metaverse. Unlike in the physical world, there are no equivalent consumer protection laws, making it essential for users to understand and inquire about the security measures employed by platform providers and property owners. Consumers should actively seek information about data collection practices, storage duration, and data deletion rights. Users should also exercise caution when sharing personal information and verify the credibility of property owners if there are any doubts. With the increasing prevalence of deepfakes and impersonations, users need to be vigilant and proactive in safeguarding their privacy and security in the virtual environment.
Gemini Consulting & Services has a team of experienced consultants who can provide a detailed guidance to enterprises on how to address cybersecurity challenges in the metaverse. Contact us to know how to implement measures to mitigate such challenges.
Considering the importance of cybersecurity within the metaverse, it is right to state that it serves as the bedrock for its sustainability and success. Here’s why.
Reputation: Trust is paramount for the metaverse to thrive, and cybersecurity plays a pivotal role in fostering this trust among platform owners and users. Given the increasing awareness of cybersecurity threats due to real-world incidents, platform owners must prioritize safeguarding sensitive user information to uphold their reputations.
Spillover Impact: While the metaverse is expanding, its influence extends beyond virtual environments into the physical world. Organizations operating within both spheres face the risk of security breaches, identity theft, or denial of service incidents in the metaverse adversely impacting their real-world reputations and operations. A positive metaverse experience on the other hand can enhance real-world business prospects.
Business Growth: In the absence of regulatory frameworks, proactive platform owners can leverage robust cybersecurity measures as a competitive advantage to attract users and drive business growth. By prioritizing secure customer experiences and influencing regulatory developments, they position themselves as leaders in the evolving metaverse landscape.
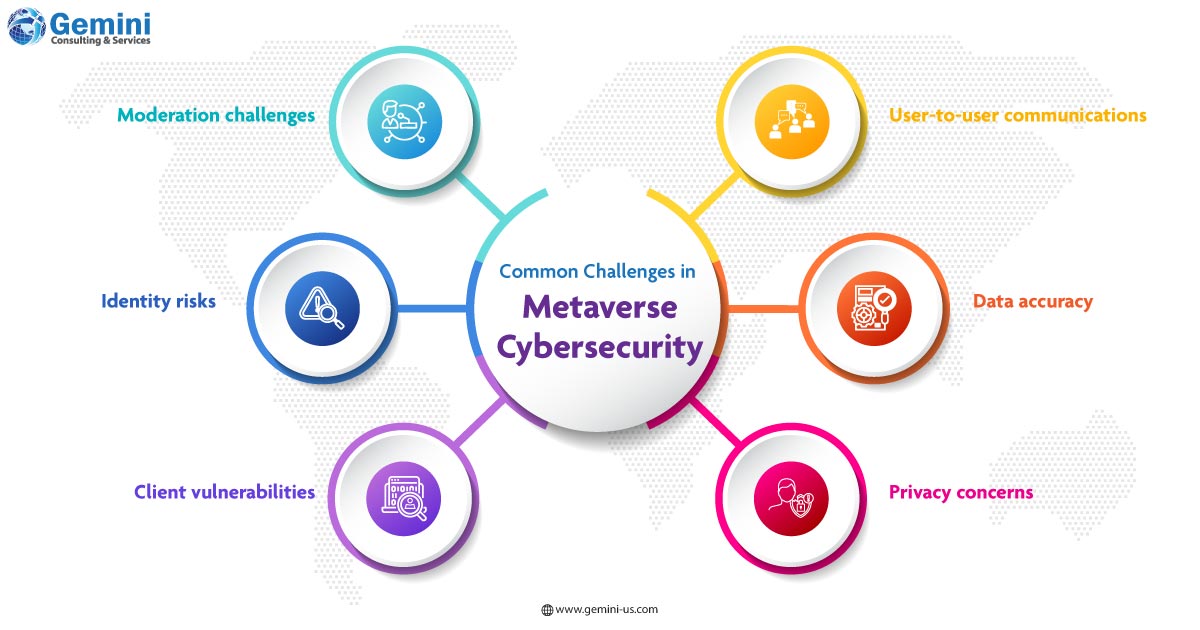
Moderation Challenges: Many metaverse platforms lack adequate support systems, leaving users vulnerable to issues like non-fungible token theft without recourse.
Identity Risks: Users face threats such as identity spoofing, account hacking, and avatar takeovers, undermining trust and security within the metaverse.
Client Vulnerabilities: VR and AR devices, being complex systems, are susceptible to various hacks and manipulations, posing risks to user identities and overall security.
User-to-User Communications: Trust-based interactions in the metaverse can be compromised by malicious actors, necessitating scalable moderation solutions.
Data Accuracy: Ensuring the accuracy of location data, product information, and user reviews presents a challenge in the decentralized metaverse environment.
Privacy Concerns: With no regulatory framework in place, privacy invasion is a growing concern as personalized experiences rely on extensive data collection, often without users’ full awareness or consent.
Addressing these challenges is crucial for establishing a secure and trustworthy metaverse ecosystem that fosters growth and innovation while safeguarding user interests.
Unique Security Challenges in VR and AR Environments
Virtual Reality (VR) and Augmented Reality (AR) areas introduce a plethora of security and privacy considerations, presenting distinctive challenges:
VR Security Challenges
Dependency: The nascent state of the metaverse lacks standardized protocols and shared services, placing users at the mercy of platform owners for ensuring the safety of their experiences. Early adopters, such as enterprises utilizing platforms like Second Life, were wholly dependent on these platforms for security, identity protection, privacy, and financial transactions.
Ownership Responsibility: Property ownership within VR environments poses numerous security and privacy dilemmas. Questions arise regarding who has access to or is restricted from these virtual properties. Can property owners dictate entry permissions? What activities are permitted within these spaces? Could illicit or financial transactions occur unnoticed?
Authentication: Verifying the identities of entities in VR environments proves challenging. For instance, in telemedicine scenarios, patients must trust that the individuals they interact with are legitimate medical professionals. Similarly, property owners must validate the qualifications of professionals before granting them access to practice within their virtual spaces.
Accountability: In cases of fraud, harassment, or abuse, determining the accountability of VR environment owners becomes crucial.
Privacy Concerns: Currently, no regulatory frameworks specifically address privacy within VR environments. Yet, given the extensive data collection and analysis conducted by metaverse platform owners, regulations are inevitable. Presently, the safeguarding or sharing of user data remains solely at the discretion of platform owners.
Advertisements: Metaverse owners wield full control over advertising within virtual spaces, similar to physical-world scenarios where advertisements can be displayed without the consent of property owners.
Privileged Accounts and Hacking: Unauthorized access to customer support or administrative accounts could result in severe compromises within VR environments, potentially impacting numerous users if left undetected.
Entry Point Compromise: Since access to the VR metaverse mainly occurs through headsets, compromising these endpoints could lead to complete control over users’ avatars.
Surveillance: Avatars’ ability to alter appearances introduces the risk of covert surveillance and intrusion into meetings, personal conversations, and other interactions without the participants’ knowledge.
AR Security Challenges
Data Integrity: AR involves overlaying third-party data onto real-world environments, making data integrity crucial. Compromised data, such as flawed location information in AR-based navigation apps, could lead to erroneous guidance for users.
Physical Security: AR users navigate real-world surroundings overlaid with virtual elements, heightening concerns about physical safety. Immersion in virtual spaces may distract users, potentially endangering themselves and others.