Enterprises battle the risk of breaching sensitive information when copying production data into non-production environments to carry out application development, testing, or data analysis. Data masking helps modify private data while protecting the original from unauthorized access by unwanted users. In this process, the structure and attributes of the data are kept intact.
Masking of data makes it impossible to identify the person (if it is personal identification) referenced in the data and prohibits reverse engineering tactics to extract such data. According to Forbes, data security is not just about access restrictions to data. It should enable the use of data effectively, securely and in a governed manner.

Oracle Data Masking
Oracle Data Masking offers end-to-end security for automation. It also allocates test databases from production in compliance with regulations. Oracle Data Masking is accessible through Oracle Enterprise Manager. Built-in SQL functions and tools in the Oracle database allow the masking of sensitive data in database tables.
How Does Oracle Manage Data Masking?
Oracle Data Masking and subsetting architecture are parts of a two-tier framework. It has a cloud-controlled User Interface (UI) or a Graphical User Interface (GUI) for administrators to handle all management-related tasks. These components can be installed locally or found on a web browser first. The Oracle Enterprise Manager framework comprises the Oracle Management Server and a database repository. The server is the core of the framework.
The Oracle Enterprise Manager (OEM) provides administrative user accounts, and processes management functions, such as jobs/events managing the flow of information back and forth from the Cloud Control UI and the nodes with Enterprise Management Agent. The Oracle Enterprise Manager Agent in turn communicates with the Management Server and executes tasks sent by Cloud Control UI and other client applications.
Enterprise Management Agents monitor all the targets and they are installed on each monitored host. Those that are running on those hosts, communicate that information to the Oracle Management Server (OMS) and manage the hosts and targets.
- First create an application data model to discover sensitive data and data relationships. This helps create or assign an application data model.
- It then selects masking formats and conditions/templates based on the nature of the sensitive data discovered.
- Data validation and previews are done using the masking algorithm and the subset reduction results.
- Carries out masking transformations by executing in-database or in-export marking and validating the data that is masked.
Given below is a typical Oracle data masking workflow.
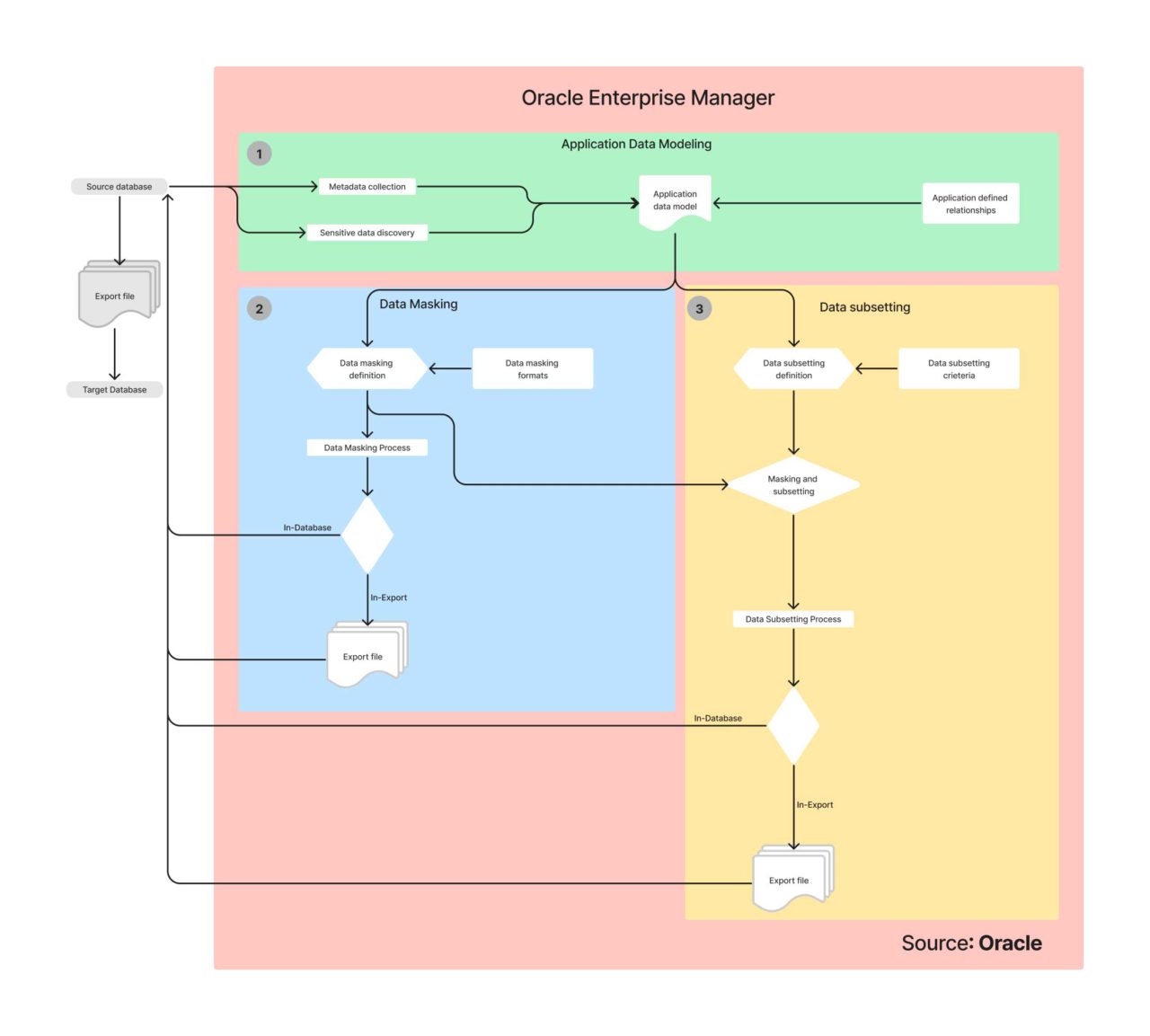
What is Application Data Modeling?
Application Data Modeling (ADM) makes the data discovery process simpler by automatically discovering Oracle database tables and mapping them with sensitive data columns. Relationships between database columns can be easily identified, and sensitive data column types can provide analytics by identifying and combining patterns in column data, names, as well as comments.
The automated discovery process can also scan databases for sensitive data and sample data in any type of column – social security/credit card information etc. Custom column types with regular expressions can also be created using Oracle’s data discovery set pattern discovery criteria to find sensitive data elements.
ADM permits businesses to first list tables, applications, and database relationships by handling sensitive data and columns. It then produces test data with data masking and subsetting.
The Centralized Data Masking/Subsetting Library
Security admins have the power to centralize definitions for masking formats while ensuring that the masking rules remain consistent across all enterprise systems regardless of the sensitive data’s location or the database. This ensures that business data has consistent marking and complies with established data-sharing standards.
With its centralized selection of data masking formats Oracle data masking format library makes it easy to handle frequently used sensitive data. For example, telephone numbers, credit card and social security numbers, and pseudonyms, there is a uniform masking format. Security admins use these masking formats in the library to specify these numbers and help database admins to utilize them across the entire organization.
The data masking format library comes with:
- Multiple built-in data masking formats / primitives that can be used in data masking definitions.
- Certain built-in masking primitives can be combined to create new formats.
SQL and PL/SQL functions for users to define when they handle complex masking formats.
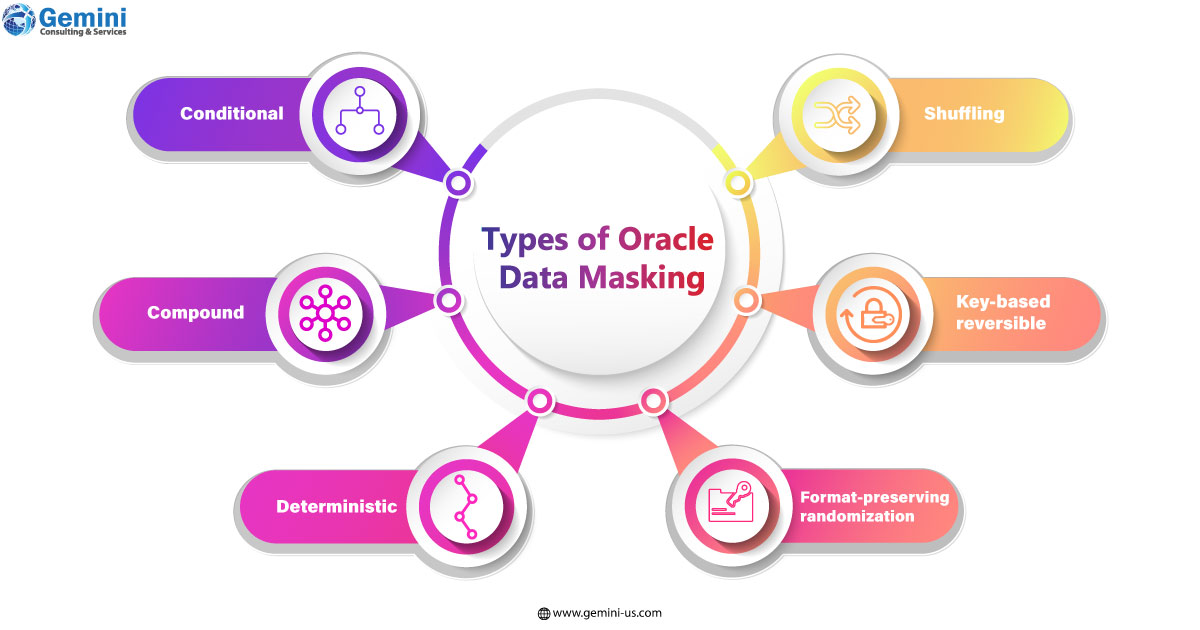
- Masking formats are the foundation of data masking definitions. Oracle offers the following masking transformations.
- Conditional data masking lets businesses mask data based on various conditions. For example, a mask that lists unique human identification numbers could be different across countries. The same can be defined accordingly in the same column.
- Compound data masking masks and groups together all related database columns while ensuring that masked data retains the original relationships of inputs. For instance, address fields in a table can be masked (i.e., city, state, country, and zip codes), with the values in the respective address field remaining consistent even after the masking process.
- Deterministic data masking is another type. It is used for getting consistent outputs across different databases for data inputs. Data and system integrity in multi-application environments can be secured with this process. This happens with a single sign-in. Say, there is a human resources application, a sales information application and a customer relationship application. While each application serves a different function, there could be common fields that may require consistent masking e.g., employee ID. This can be handled using substitution and encryption formats.
- Shuffling randomly re-arranges the fields in a table column thereby breaking mapping between data elements. For example, health records could be shuffled to mask personal health information.
- Key-based reversible data masking allows for decrypting and encrypting of raw data with secure key strings. It can also preserve the original format of inputs. This leverages a 3DES algorithm to enable masking to send data to third parties for analysis, auditing, etc. This processed data once received can be recovered using the same key strings that were used to encrypt it.
Format-preserving randomization basically randomizes and preserves the original format of the input data (length, special characters, the position of numbers/characters, upper/lower cases).
Simplified Data Subsetting ProcessThe data subsetting process of Oracle uses defined goals and conditions to simplify the data. It is possible to subset data on any goal. If the business wants to extract a 1% subset of the entire database table with 100,000 rows to create a table with 1,000, it is possible. Similarly, it can be done using time-based conditions. If all records need to be destroyed before a specific date in a specific region, it can be done.
Businesses can obtain real-time, dynamic views of an application schema with all details such as before and after file sizes, the percentage of the data subsets, and dependent tables. These views are then used by administrators to validate criteria for further data subsetting tasks.
Partner with Gemini Consulting & Services to unlock maximum value from data and minimize risks with Oracle Data Masking. Contact us to know how Oracle Data Masking can help your enterprise to securely handle data.Out-of-the-Box Application Templates
Previously identified sensitive data columns are provided by Oracle data masking applications. It also offers details of the relationships. It supports intuitive masking methods that comply with industry standards as well as establishes best practices for packaged Oracle applications like Fusion, E-Business Suite etc. A self-update feature lets businesses make the best use of Oracle’s latest data subsetting and masking templates.



