As businesses expand, the emphasis on organizational structure grows, leading teams to engage in larger projects and increased workforce expansion. Consequently, managing the influx of data becomes more crucial. While tackling risk management might initially appear daunting, it is imperative for efficiently handling data that requires processing and secure transmission. This involves considering factors such as roles, privileges, and access points.
Regrettably, many organizations tend to overlook the importance of incorporating access controls during ERP implementation or upgrades. Some delay the integration of risk management from the project’s outset. However, including these controls during the ERP project implementation phase not only establishes a resilient role framework for resources but also effectively mitigates security vulnerabilities, averting concerns from auditors.
According to Forbes, the risk function can provide valuable recommendations for enforcing effective controls to ensure data privacy and security across both physical and virtual environments. This, in turn, supports the organization in maintaining a coherent cloud strategy.
Oracle Fusion Cloud Risk Management and Compliance
Oracle Fusion Cloud Risk Management and Compliance is one of the central pieces in Oracle Cloud ERP that offers a set of capabilities required to protect a business against risks and compliance challenges. It can automate the analysis, monitoring, and regulation of ERP transactions as well as configurations, and security. Being a part of Oracle ERP, the Oracle Risk Management Cloud leverages advanced data science and AI/ML systems to bring about secured roles, handle Segregation of Duties (SoD) conflicts, track sensitive configurations, and identify suspicious transactions.
Oracle Fusion Cloud Risk Management and Compliance (RMC) can safeguard against human errors by easily identifying anomalies in transaction processing, thereby, identifying fraud or errors that could have a significant impact on financial results.
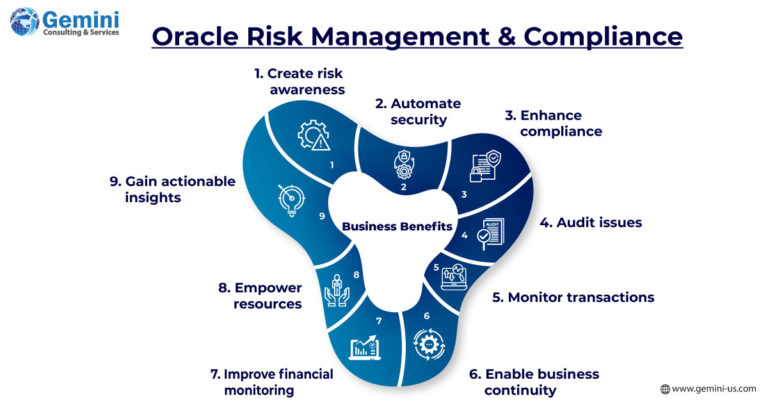
Oracle Risk Management and Compliance offers AI-enabled tools for risk analysis. These tools help enterprises to:
- Enhance risk awareness, transparency, integration, and accountability of handling data.
- Automate security and transaction data analysis for Segregation of Duties (SOD), fraud, manual errors, and policy violations.
- Deploy best practices for risk management and compliance using pre-built algorithms to target and track high-risk areas.
- Avoid expensive user acceptance testing and audit issues by designing secure ERP roles before applications go live.
- Do away with tampering by monitoring transactions and ERP data with built-in AI.
- Enable business continuity and resilience by driving an AI-driven approach to risk management and security.
Improve financial monitoring and analysis by linking risk to business results. - Empower resources to balance opportunities with risks and streamline the same with business objectives.
Gain actionable insights and deploy remediation solutions.
Oracle RMC Modules: Unveiling Powerful Capabilities
Within the Oracle Risk Management and Compliance (RMC) module, an array of robust features awaits, geared towards enhancing control and oversight.
One notable facet of Oracle RMC lies in its advanced access controls, a crucial tool for businesses aiming to pinpoint instances of excessive user-role assignments. These assignments, often characterized by users wielding undue influence through their application roles and privileges, can impede streamlined operations.
For instance, consider users with the ability to both create and approve critical processes like product or report submissions. In such scenarios, their unfettered access can needlessly hinder the organization’s review process, introducing unwarranted risks. Similar logic applies to other privilege and role-based combinations, where the goal is to strike a balance between access and security.
Oracle Advanced Financial Controls emerges as a potent asset, arming organizations with the ability to unearth potential risks such as fraud or transaction errors carried out through Oracle Cloud applications. By leveraging user-designed models, coupled with filters defining suspicious or fraudulent transactions in alignment with the organization’s rules and policies, risks are swiftly flagged.
The audit role is not left untouched within this landscape. It opens avenues for constructing transaction models that assess risk levels exhibited by systems, drawing upon the auditor’s expertise and familiarity with financial risk. This process assumes paramount significance as it can define the success or downfall of a business, particularly in the context of external audits and regulatory inspections.
Furthermore, Oracle RMC Cloud introduces a secure role design mechanism, streamlining security analysis at the privilege level during job role configuration. By doing so, it effectively sidesteps the need for costly redesigns, rework, and delays during ERP implementation.
Oracle Fusion Cloud Risk Management and Compliance steps in as a vigilant guardian, facilitating the swift detection of anomalies within transaction processing. This capability extends to tracking instances of fraud or errors, potentially sparing businesses from significant financial repercussions.
For those seeking an agile and flexible security solution, partnering with Gemini Consulting & Services for the deployment of Oracle Fusion Risk and Compliance Management presents a viable option. For a comprehensive understanding of how to safeguard your data through Oracle Fusion Cloud Risk Management and Compliance, contact us.

Continuous Transaction Monitoring: Businesses gain the power to consistently oversee ERP transactions. Business process auditors can swiftly spot potential high-risk scenarios, such as the creation of duplicate invoices or unauthorized resource utilization. With the aid of a user-friendly visual workbench, they can even develop new algorithms and handle exceptions seamlessly through a straightforward workflow. The incorporation of compensating controls allows for the identification of transactions linked to the misuse of excessive privileges.
Centralized Policy Repository and Workflow: The solution acts as a centralized hub for all corporate policies, delivering a comprehensive end-to-end workflow solution. This proves invaluable by automating a range of crucial processes, including internal audit assessments, financial reporting certifications, and compliance with regulatory mandates. Moreover, it streamlines data protection assessments, certification, and continuous monitoring of employee access to sensitive information. The capability to report data breach incidents further enhances its utility.
Privilege and Data Protection: Oracle Risk Management ensures the safeguarding of privileges and sensitive data through regular certification of access privileges. By automating workflows, the system alleviates the burden of manual compliance tasks that traditionally rely on spreadsheets and emails. Administrators can meticulously supervise sensitive ERP roles and users, facilitating approval processes conducted by designated process owners. The feature of access certification, in particular, streamlines periodic reviews within the organization.