Enterprise organizations today face a multitude of security threats in the digital landscape, posing risks to data integrity and business continuity. Recognizing this challenge, Microsoft has introduced generative AI technology to its suite of solutions. Leading the way is Microsoft Security Copilot, a groundbreaking service built on GP-4 architecture. This innovative tool empowers teams to effectively combat modern data security threats.
Microsoft Security Copilot is specifically designed to enhance the capabilities of security analysts, enabling them to detect vulnerabilities that might otherwise go unnoticed by traditional tools. By simplifying complex data and providing training on best practices, the tool equips analysts with valuable insights and resources.
According to Statista, a staggering 25% of global data remains vulnerable to security threats due to insufficient protection. This number is expected to rise to 45% by 2025. Considering these statistics, Microsoft Security Copilot emerges as a crucial solution for safeguarding sensitive information.
Microsoft Security Copilot
An intelligent AI-powered security tool, Microsoft Security Copilot revolutionizes how enterprises address cybersecurity challenges. By leveraging cutting-edge technology, it empowers security analysts, provides valuable insights, and strengthens organizations’ ability to proactively protect their digital assets.

Integrating multiple Microsoft technologies, Security Copilot serves as an intelligent assistant, catering to a wide range of security-related concerns. From basic inquiries to intricate technical questions, the tool offers guidance and support, positioning itself as a game-changer in the realm of cybersecurity. Its comprehensive platform assists with vulnerability management, incident response strategies, and overall performance optimization for security professionals navigating the ever-evolving digital landscape.
Key features of Security Copilot include its ability to respond to natural language queries, guide teams in incident remediation, perform threat-hunting tasks, and generate detailed security reports. Leveraging advanced AI capabilities, it efficiently analyzes vast amounts of data from various sources, providing actionable insights that empower stakeholders to make informed decisions. By actively monitoring online traffic and highlighting malicious activities, the tool accelerates threat intelligence comprehension, enabling security teams to manage complex security scenarios with greater efficiency.
The user interface of Security Copilot is intuitive and designed with a dark-themed aesthetic, ensuring ease of use and accessibility for users. It engages security experts within the organization, facilitating incident investigations, delivering concise event summaries, and streamlining the reporting process. Through continuous user feedback, the tool evolves and improves its skills over time, further enhancing its effectiveness.
Microsoft Security Copilot is a cutting-edge tool that empowers resources to address data security issues in a scalable manner. Gemini Consulting & Services can help organizations to drive innovation with Microsoft Security Copilot. Contact us to know more about AI-enabled features of Microsoft Security Copilot.
Features of Microsoft Security Copilot
- Simplified security operations with an innovative prompt bar that enables users to ask questions in natural language.
- Greater control and a transparent system of maintaining data are encouraging as the platform maintains an accurate audit trail of all prompts and responses. This helps investigations to be reviewed if needed.
- AI-driven insights as Copilot is equipped to analyze and respond to prompts using both external and internal data sources within the organization. Users can view summaries of vulnerabilities ensuring an all-around understanding of potential security threats. The prompt can also be edited to adjust the response if required.
- Collaboration and Continuous Improvement by way of efficient collaboration, exporting, and sharing results across teams in a secure manner. Despite being reliable, the system allows users to provide feedback on incorrect, unclear, or incomplete responses to continually improve its performance, in the event of a mishap.
- Prompt Books enhance automation and sharing of knowledge by collecting prompts into a structured set of steps developed by the user.
The platform integrates with Microsoft Security products and is slated to soon embrace third-party products as well.
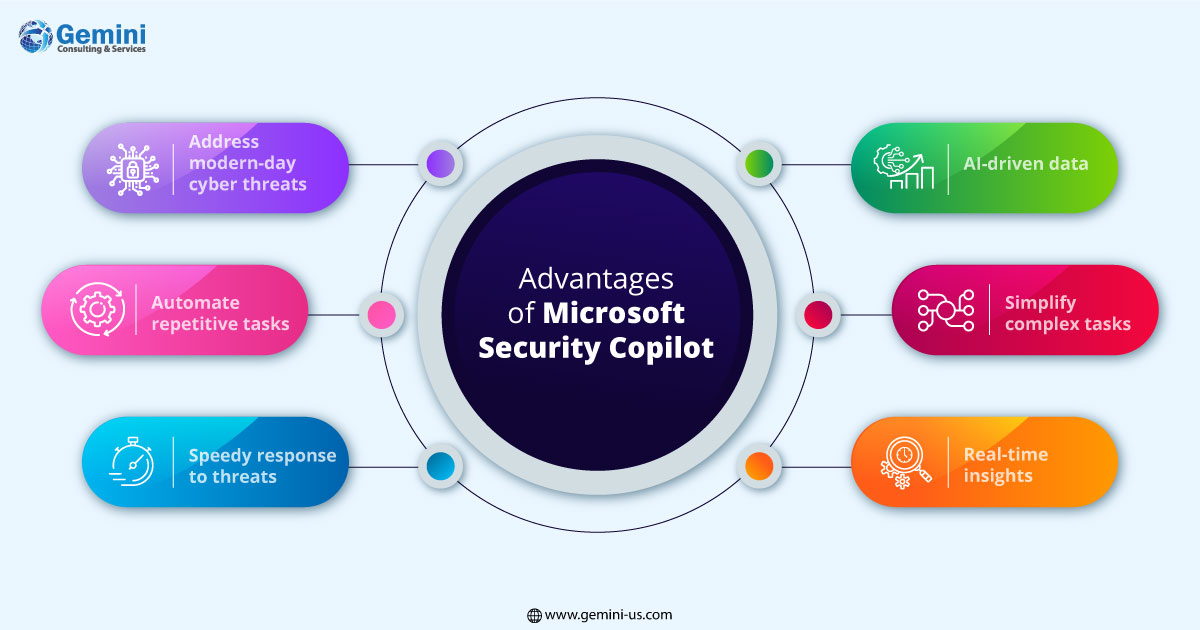
- Security Copilot augments human efforts and the capabilities of security resources by providing AI-driven insights, helping them make clear informed decisions and handle threats quickly.
- AI helps security teams simplify complex tasks such as threat detection and response.
- The use of ChatGPT helps provides provide domain-specific data and real-time insights that empower every resource in the team.
- Security Copilot enables resources to detect and respond to threats at the speed of a speed, significantly reducing the time required to address security violations.
- The tool automates repetitive tasks and provides contextual recommendations for analysts to progress toward higher-level decision-making and investigation.
- Cutting-edge tech used by Copilot help amplify capabilities to address modern-day cyber threats.
How Microsoft Security Copilot Enhances Cybersecurity?
The benefit that stands out in Microsoft Security Copilot is its ability to provide prompt-based cyber security detection and almost immediate remediation functionality using GPT-4. Complex threats can be identified, analyzed, and resolved before consequences arise. Microsoft Security Copilot offers an extensive knowledge base that analysts can refer to. As a result, enterprises can use the tool to fill the cybersecurity skill gap of their internal security experts. The prompt book feature helps users combine multiple actions or automation into a single prompt or button thereby reducing the wait time for resolution. Users can also generate a PowerPoint deck that details occurrences and potential entry points for attackers.